According to Statista, the average cost of a data breach globally increased to 4.35 million dollars in 2022 from 4.24 million dollars the year before. Organizations need precautions or tools to protect their sensitive data from a breach. That’s where data masking tools come in.
Data masking tools protect an organization’s sensitive data from a potential breach by masking customers’ data. The data mainly contains credit card numbers, social security numbers, bank accounts, location, and other personal information with fabricated characters.
Data masking solutions along with data discovery tools can prevent sensitive data from being accessed by anyone not authorized to view it. It eventually saves the organization from data and business loss. These masking tools obfuscate the data fields using encryption, shuffling, and replacement. Data masking is a one-way procedure since it makes accessing or reversing original data nearly impossible.
Data Bridge Market Research shows that the data masking market is predicted to develop at a Compound Annual Growth Rate (CAGR) of 13.07% between 2021 and 2028. By 2028, this increase is expected to result in a market value of USD 1,268.08 million.
The most recent tool includes a virtual masking feature. In real-time, information is dynamically given in a masked state from a live database whenever users need it. This process is called dynamic masking.
We have reviewed ten top data masking tools in this article. These are the best and most widely used data masking tools for small, large, and mid-sized businesses. Before diving into this, let’s check out the standard features of data masking solutions.
Features of Data Masking Tools
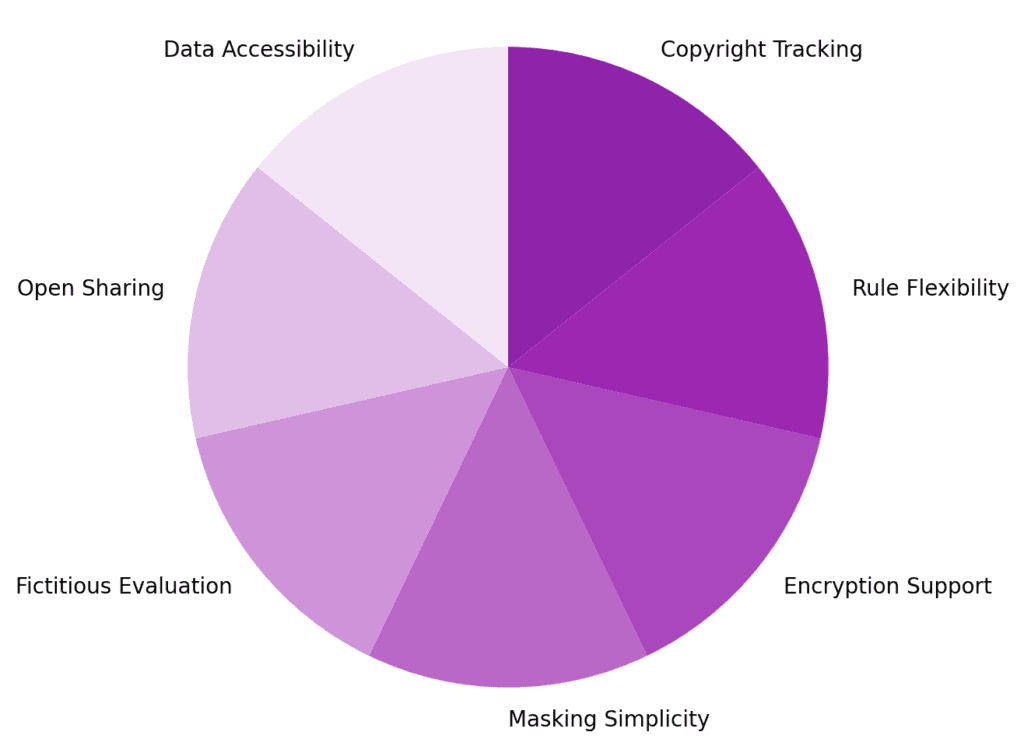
- Data from various databases should be accessible
- All data sources in the software must be open for sharing
- For evaluation, accurate but fictitious data should be available
- Masking rules should be simple to set up and are not governed by codes
- These tools must enable encryption conversion with format preservation
- Data masking tools can apply different rules to the main set and subsets of data
- Provide an efficient approach for tracking copyright law conformance
10 Popular Data Masking Tools and Software in 2024
DATPROF
Users can hide or encrypt production data with DATPROF privacy to safeguard client data while allowing software developers to use relevant test data. It has a patented approach for subsetting databases directly and reliably. The program can handle complex data associations because of its user-friendly interface.
Features
- Compatible across various apps and databases (e.g., Oracle, Microsoft SQL Server, DB2 iSeries, DB2 LUW, Postgres)
- Compatibility for XML and CSV files
- Artificial data generators are built-in
- GDPR monitoring and HTML audit
- REST API is used to automate data testing
- Provisioning is made simple with the use of a web interface
| Pros | Cons |
| Excellent performance with big data sets | Literature is only available in English |
| A trial version is available for download | Creating templates necessitates the use of Windows |
| Simple to set up and utilize | Templates can be run on either Windows or Linux |
| All popular database systems are supported natively |
More About DATPROF
Website: DATPROF
Delphix
Delphix is a data masking solution for hiding data across the corporation that is quick and secure. The Delphix Masking Engine uses a Delphix data virtualization platform to conserve and save data loading. DDM exists as a result of a joint venture with HexaTier.
Features
- End-to-end data masking is performed, and reports are generated as a result
- Data masking is simple to employ because no training is necessary
- It consistently relocates data among sites, whether on-premises or in the cloud
- It generates HIPAA, PCI DSS, and SOX rules that are encoded
| Pros | Cons |
| Recovering records is quick and straightforward | Expensive |
| Database virtualization | SQL Server databases are sluggish and have a restricted number of features |
| Data refreshes quickly | Relies on obsolete NFS protocols |
More About Delphix
Website: Delphix
Documentation: Delphix Products

IRI FieldShield
IRI FieldShield is well-known in the DB data masking and testing data market for its fast performance, low cost, compliance capabilities, and wide range of supporting data sources. For data masking, troubleshooting, ETL, data integrity, and analytical tasks, the IRI FieldShield provides excellent performance without using a central server.
Features
- Data profiling, finding (search), and segmentation from several sources
- De-identify and conceal PII using various masking techniques (including FPE)
- Ensures integrity constraints in multi-DB/file and schema contexts
- Integrated re-ID risk rating and audit for GDPR, HIPAA, PCI DSS, and other regulations
| Pros | Cons |
| Accessible metadata and many visual job design choices | Field Shield API call or expensive socks proxy solution is required for DDM |
| It provides high performance without the need for a central server | Only 1NF data structure is supported |
| Reliable and cost-effective assistance | Dark Shield is required for BLOBs and other large files |
More About IRI FieldShield
Website: IRI FieldShield
Documentation: IRI
Immuta
Immuta is a cloud-based tool that gives data development and operational teams a single place to manage analytical data. Data-driven enterprises use Immuta all over the globe to reduce data access time. With Immuta you can securely exchange more information with multiple users, and reduce the risk of cyber-attacks.
Features
- Subsetting
- Dynamic data masking
- Static data masking
- Data Redaction
| Pros | Cons |
| Platform compatibility is extensive | Data Sources cannot be query-backed |
| Unlock new analytical use cases | |
| Data can be shared across teams |
More About Immuta
Website: Immuta
Documentation: Immuta Docs
Oracle – Data Masking and Subsetting
Oracle offers a variety of transformation processes for hiding data from various use cases under multiple scenarios. It has quick, reliable security and can manage various data sources. This utility has a low impact on the system and uses few resources.
It focuses on data protection, compliance, and ensuring that masked versions are accessible to the development and testing teams. Within the database, this tool instantly detects confidential material and its offspring. It keeps a centralized collection of masking patterns on hand, with ready-to-use masking forms and many alternatives for disguising any dataset.
The Semantics Database Model (SDM) is supported by this software, available in the cloud, and can be deployed on Mac, Linux, and Windows platforms.
Features
- Instantly find sophisticated data and its links
- Improved application designs
- Large concealing design repository
- Full data masking mechanism
| Pros | Cons |
| It offers several data masking methods | The cost is high |
| It also works with databases that aren’t Oracle | Production and experimentation platforms are less secure |
| Take less time to execute |
More About Oracle – Data Masking and Subsetting
Website: Oracle
Documentation: Oracle Data Masking
Informatica Persistent Data Masking
Informatica Persistent Data Masking is a user-friendly data masking tool that aids IT organizations in accessing and managing their most complex data.
It gives many databases with business scalability, ruggedness, and integrity. A unified inspection trail offers a reliable data masking policy for the entire industry. It allows comprehensive monitoring tools and records to track activities and protect confidential material.
Features
- Comprehensive data masking is supported
- From a central site, it develops and combines the masking procedure
- Functions for dealing with an extensive database
- It has a wide range of connectivity options and customizable application support
| Pros | Cons |
| A unified audit trail reduces the possibility of data breaches | The user interface needs to be improved |
| It helps improve the efficiency of research, development, and training activities | |
| Desktop deployment is straightforward |
More About Informatica Persistent Data Masking
Website: Informatica
Documentation: Informatica Docs
Accutive’s Data Discovery & Masking
Accutive’s Data Discovery and Data Masking (ADM) technology allows you to find and hide your data while keeping data properties and fields intact across numerous sources.
Data discovery swiftly finds sensitive datasets using pre-configured, adjustable compliance standards or user-defined search phrases. You can use your ADM findings in your data masking configuration or construct your own.
The data will display after the masking mechanism has filtered it, but it will be bogus. Furthermore, confidential information will be constant throughout all sources.
Features
- Allow for quick detection of personal documents that must comply with regulations such as GDPR
- Across different databases, the capability to reliably and consistently mask source data to the same value
- Any significant source kind, such as Oracle, can transport data to any essential transit type
- Data masking should be a part of your computational workflow
| Pros | Cons |
| Easy to configure and use | Groovy scripting to alter application behavior necessitates basic programming skills |
| Built-in progress indicator for quickly masking settings | Only available in English, French, and German |
| Reliable and cost-effective assistance |
More About Accutive Data Masking
Website: Accutive
Microsoft SQL Server Data Masking
It masks the data securely retrieved from the system using dynamic data masking techniques. Complete, basic, random, and email are the four forms of masking available in SQL Server.
The type chosen is determined by the sort of data to be concealed. Microsoft’s inherent capabilities in the product line, solutions, consultancy, and customer focus motivate organizations to choose this solution.
Features
- By safeguarding data, it is possible to simplify the design and code for the application
- It does not alter or manipulate the database’s stored contents
- It allows the data administrator to select the amount of complex information to disclose while minimizing the application’s impact
| Pros | Cons |
| End users are not allowed to visualize large amounts of data | When accessing databases as a privileged user, data is fully exposed |
| Using a mask on a table field will not prevent updates | Masking can be removed using the CAST function and an ad-hoc query |
| It is not necessary to make changes to applications to read data | Masking is not possible for Encrypted columns |
More About Microsoft SQL Server Data Masking
Website: Microsoft
Documentation: Data Masking
IBM InfoSphere Optim Data Privacy
InfoSphere ensures the privacy and data protection required by the finance business, particularly in the multi-vendor development or support environment. Data extraction from the database server and masking methods are simple and need no code. In a security gateway, the transformation happens at a faster rate. Business results, risk assessment, data safety, and process efficiency are all improved by IBM.
Features
- Reduce risk by encrypting data
- Enhance the data protection performance
- Provides a safe environment to test applications
| Pros | Cons |
| It’s simple to abstract data without programming | The user interface needs to be improved |
| Allows you to mask data in a variety of ways | A complex structure |
| Capabilities for intelligent filtering |
More About IBM InfoSphere Optim Data Privacy
Website: IBM
Documentation: IBM Docs

IRI DarkShield (Unstructured Data Masking)
IRI DarkShield detects confidential data in various “dark data” sources simultaneously. The DarkShield API delivers the same filtering and disguising capabilities for apps and web services. It operates with unlimited data streams and allows for task allocation flexibility.
Features
- Built-in data sorting with the capacity to explore, hide, and publish simultaneously
- There are a variety of search algorithms and masking functions available, like fuzzy match and NER
- It links with SIEM/DOC environments and numerous log formats for auditing
| Pros | Cons |
| Fast speeds, multi-source; no requirement to hide data in the cloud or give up data security | OCR limits independent and integrated image abilities, which may require tuning |
| In both unorganized and organized data, a constant ciphertext ensures integrity constraints | Pricing alternatives may appear complicated in mixed source data and use case settings |
| FieldShield includes data types, masking methods, the engine, and the work design GUI |
More About IRI DarkShield (Unstructured Data Masking)
Website: IRI DarkShield
FAQs
Which data masking tool provides a custom masking ability for the user?
Oracle Data Masking and Subsetting allow you to create customized data masking scripts. Users can complete data subsetting definitions to define table rules and parameters.
Who has got the best masking software reviews?
According to G2:
- Immuta
- Informatica dynamic data masking
- LiveRamp
According to Gartner:
- Microsoft SQL server
- Infosphere
- Delphix
List down the best data masking vendors.
According to Gartner:
- Microsoft
- MENTIS
- IBM
- K2View
- Imperva
- Delphix
Who is the most famous data masking company?
Top data masking companies are:
- Delphix
- Evince Technology
- IRI, The CoSort Company
- Solix Technologies
- BlueTalon
Which is the most commonly used Data Masking tool in the financial industry, and why?
In the financial sector, DATPROF Privacy is used. It offers a free trial as well as premium consulting and integration services. DATPROF Privacy hides your test data and replaces it with fictitious data.
Which Data Masking tools are cost-effective?
Persistent Data Masking in Informatica is relatively cost-effective.
Conclusion
Data masking tools shield an organization’s confidential data by masking personal data with fake characters and presenting the desensitized data securely in a non-production environment.
These masking tools protect the organization from potential data breaches, loss of reputation, and regulatory and commercial loss by preventing accurate personal information from being accessed by anybody who cannot view it.
Evaluation of the right data masking solution depends on the following:
- The quantity of the data
- Projected requirements
- The private data discovery process
- Cost and data management features
- Vendor to meet all of these requirements
The global market for data masking solutions is expected to expand significantly in the coming years. This is due to rising demand for data privacy and security, compliance with regulations, and the need to safeguard sensitive data. As a result, investing in data masking solutions can assist organizations in protecting their data and maintaining customer confidence, both of which are critical for company success.
Image Source: Bich Tran, Tuur Tisseghem, Danny Meneses

1 comment
In-depth details for data masking thanks Zawya